
Maybe your network is slow, or you’re getting calls from your ISP for illegal music downloads. No matter the circumstance, the culprit could be a nearby user stealing your network access.
We’re going to look at four different methods for finding other users on your network – users that don’t belong there and should be revoked of their access. There may be unwelcome computers getting free Wi-Fi from you. We will look at what is needed to secure the network with a wireless network password.
Check Who is Using Your Wireless Network
Some programs can scan your entire network to see who else is on it. This is the easiest way to simply check if it’s being used before beefing up the security.
Wireless Network Watcher
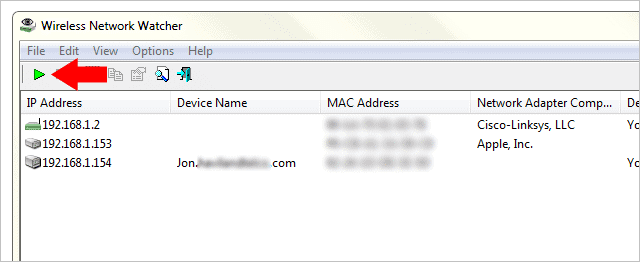
Wireless Network Watcher does a simple job of scanning the network to see who else is using it. This includes not only the wireless but also the wired connections. The above image shows a router first, then an iPhone, and a wired desktop for the final machine. Export these results from “View > HTML Report – All Items.”
If the range the program automatically detects isn’t correct for whatever reason, press the “F9” key to open the advanced options. It’s here you can enter a specific IP range to scan.
Fing – Network Scanner
Fing is a network scanner for mobile devices. The app is free and simple to use – just launch it to find what devices are using your wireless network. The scan will begin immediately.
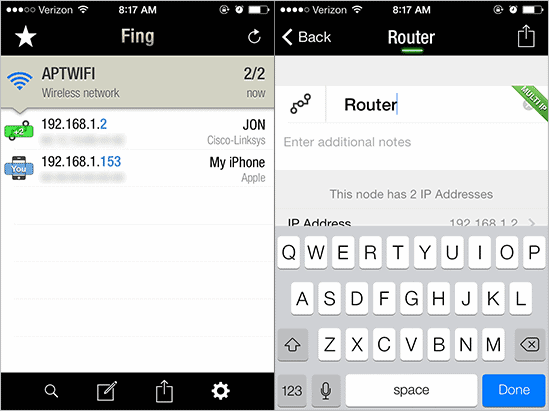
You can then select devices you know the identify of and rename them in case you scan them again in the future. Press the send button at the top right to send the results of any of the machines to a network admin or someone who can help identify any rogue machines that need to be inspected.
Note that you must be connected to your Wi-Fi network for this to work. It’s a practical mistake to be connected to a cellular network in your home while wondering why the results aren’t populating. “Settings > Wi-Fi” on the iPhone is where you’ll find these options.
SoftPerfect Network Scanner
Network Scanner isn’t as easy to use as those prior in this list, but it can help show if another user is on your network given the other methods don’t work.
You must first identify the IP address of your default gateway. Open “CMD” from the start menu and enter “ipconfig” like below.
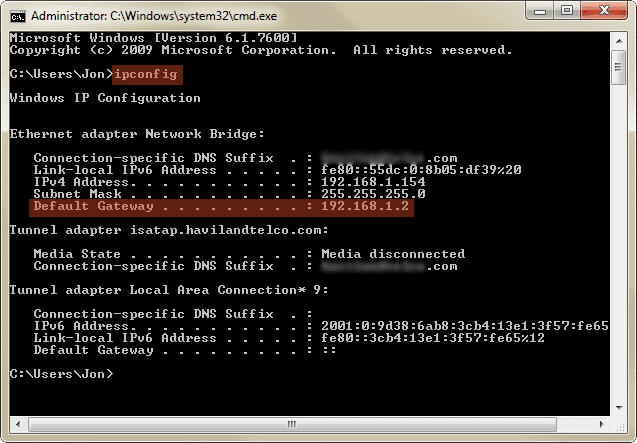
You’re looking for the address of the default gateway. Ours is “192.168.1.2.”
Now open Network Scanner and enter the default gateway in the first field. Enter the same address in the second field but with “255” as the final value. This will scan every device that’s populated from the router. Press “Start Scanning” to begin the scan.
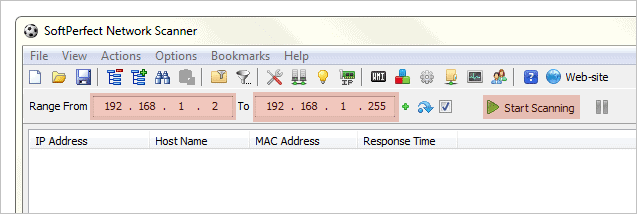
The machines will display with their IP and MAC addresses. We can see our default gateway is the first on the list, followed by the desktop we found with Wireless Network Watcher from above, and finally we have another device that isn’t identified with anything. We know, however, that this is an iPhone as described with the Fing app.
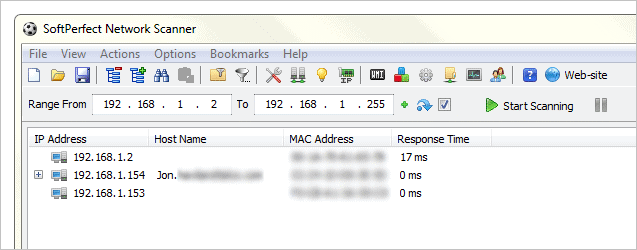
Press “Ctrl + S” to save these results to a file.
DHCP Table from the Default Gateway
Instead of using these programs above, we can easily see what devices have been connected to the wireless router by accessing the DHCP reservation table.
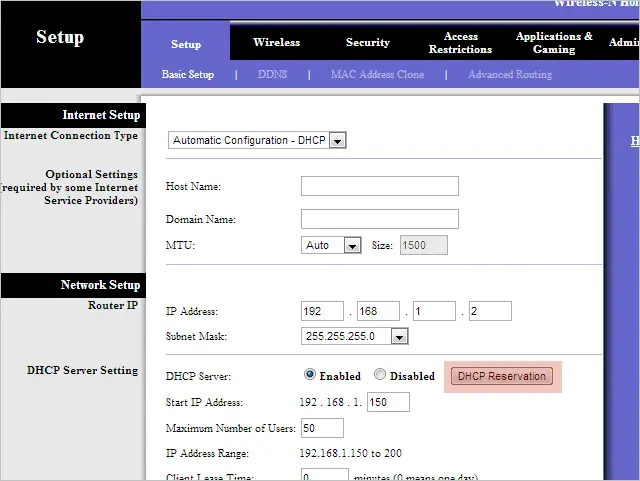
Read the step above on finding the default gateway from the command prompt, and then enter that address as the URL in a browser. If you have a password set to protect your router settings, you’ll need to enter this in now.
Upon loading the interface, look for something called “DHCP Reservation.” In our Linksys WRT150N, it’s in “Setup > Basic Setup.”
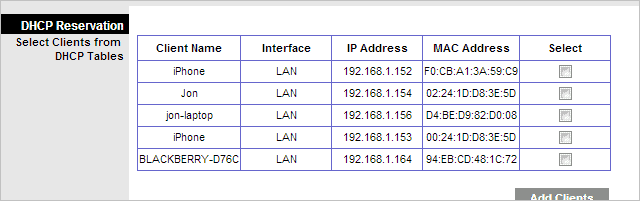
This table shows users that have connected to the router. My particular table has two iPhones, a desktop, laptop, and BlackBerry.
Now that we know who is leeching off of our network, its time to put an end to this stealing.
How to Secure Your Wireless Network
We looked at four different methods of finding other users connected to a network. While it’s informative for merely numerical purposes, it’s difficult to actually identify who these users are.
If you only have one computer and no mobile device, then the methods above, like with Fing, that show an iPhone attached to your network, should prompt some worry that someone is using your network free of charge. The best way to combat this is to secure the network with a wireless password.
Secure a Wireless Network With a Password
The wireless security settings for my particular router is in “Wireless > Wireless Security.” This setting should be in a similar path for all routers. Choose a security mode, encryption type, and password. This is all that’s needed to secure a wireless network.
A common security mode is WPA, so I’ve chosen “WPA2 Personal.” I’ve chosen either encryption method the router allows: “TKIP or AES.” Then just enter a unique password.
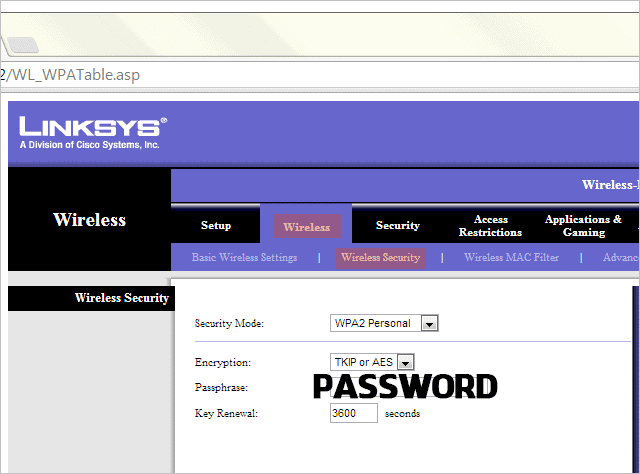
If you’ve already done all of these steps, yet someone is still using your wireless network, simply change the password to something entirely different. This will force them to enter the new password upon using your network. Without the new password they will be rendered incapable to use the network.
Only Allow Certain Computers Access with MAC Filtering
In addition to a wireless password, you could configure the router to permit only particular MAC addresses from connecting.
My MAC filtering section is under “Wireless > Wireless MAC Filter.”
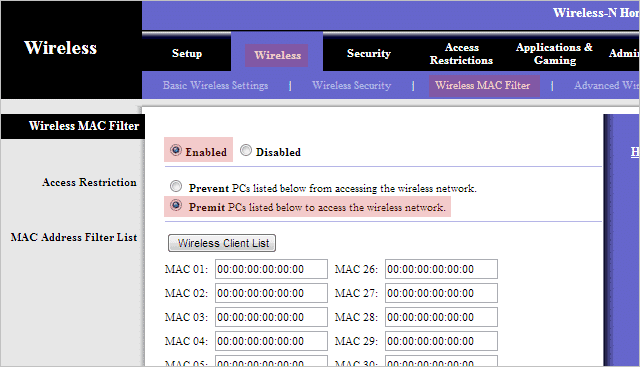
Now you’ll need to identify the MAC addresses of the computers you want to allow. If you’ve only got a few, this shouldn’t be a problem. You can do this either by using one of the aforementioned programs or via a command prompt by entering “ipconfig /all” and looking for a value next to “Physical Address,” like so:
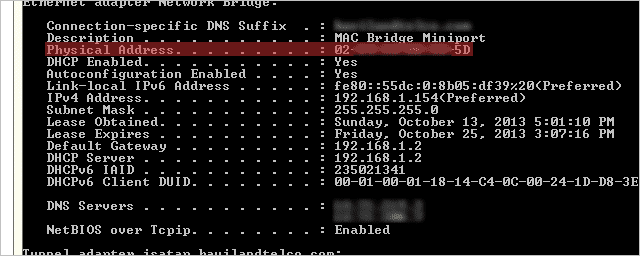
This address needs to then be entered in the settings of the router. If only this address is submitted, it’s the only computer that’s allowed on the network. You’ll need to perform the same steps for other devices to give them access.
Conclusion
While the programs we mentioned may not provide a plethora of specific details for the connected devices, they will still help make a decision as to whether a device is connected that’s not your own. It’s then that you can implement or change the wireless security settings to combat the breach.







